- Posted on
- Bhanu Pratap
What is a secure cloud migration?
A security-first approach to cloud computing means being prepared from the beginning. It’s not only about setting up tools or running scans once in a while. It’s about knowing where the risks are, keeping an eye on them, and putting systems in place that can respond automatically and rightly when something feels off. It helps us stay ahead of threats before they turn into problems, and the way to do that is through clear policies, tested processes, and automation that manages every process in the background.Components of a secure cloud migration
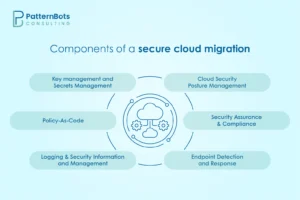 There’s no shortcut to a secure setup, but there is a clear structure. Here are six major components that cover both the technical and strategic layers needed to make your cloud migration secure right from the planning stage.
There’s no shortcut to a secure setup, but there is a clear structure. Here are six major components that cover both the technical and strategic layers needed to make your cloud migration secure right from the planning stage.
1. Cloud Security Posture Management
Every cloud service provider has a minimum set of security and compliance requirements for the resources we store in the cloud. Cloud Security Posture Management can read and ensure that your cloud configurations comply with these best practices and notify you of the issues in case of remediation. Moreover, they can also identify configuration drifts occurring due to threat attempts. Thus, it is to be ensured that your cloud environment has a CSPM tool so that the migration meets all the security and compliance requirements. Ideally, Level 3 or higher NIST Cybersecurity should be selected for better security assurance.2. Endpoint Detection and Response
EDR (Endpoint Detection and Response) is a cybersecurity technology that monitors user devices for detecting threats related to ransomware and malware. During cloud deployment, each virtual machine should have Endpoint Security installed, as it helps in preventing unauthorised access to critical systems. Thus, for a secure cloud migration strategy, you should make installation of EDR tools on all the virtual machines compulsory by enforcing it through a CSPM solution and policy as code.3. Key management and secrets management
The cloud migration plan should have a strategy for securing and protecting the sensitive configurations. To do so, you can store the secret configurations in a central location by using a cloud-based secret management service. It can help in securely storing, transferring, and managing important data like passwords, API keys, certificates, encryption keys, tokens, SSH keys, and database credentials. To support this, you can pair key management with a FIPS 140.2 hardware security module. However, you should also ensure that the hardware module supports this system for secured key storage and retrieval.4. Policy-as-code
The idea behind using policy-as-code is writing code in configuration-based language for easily managing and automating policies. There are some rules that you should follow while implementing policy-as-code. These are:- Do not use public IPs on Virtual Machines
- For storage purposes, use the encryption keys provided in key management solutions.
- For every API and web application, you should use a firewall to detect and block intrusions.
5. Logging and Security Information and Event Management
SIEM (security information and event management) technology collects and assembles event log data from different sources and helps in identifying unusual activities. SIEM systems minimise the chances of cyberattacks by tracking the patterns of users, limiting attempts of access, and preparing compliance reports. By integrating your cloud deployment with an end-to-end SIEM solution, you can analyse log data for each and every component of your architecture. There are some highly recommended SIEM systems that you can use for this purpose, like IBM Security QRadar, FortiSIEM, Datadog Security Monitoring, and AT&T Cybersecurity.6. Security assurance and compliance
Cloud service providers should ensure compliance with standards like PCI Data Storage Solution, SOC2 Type II, and ISO127001. With these certifications, you can create a baseline for the security assurance and compliance requirements. While structuring your work with the compliance, focus on these two deliverables:- Make sure that you have a CIS Benchmark score for every infrastructural element.
- Check your environment with the NIST 1.1 Cybersecure framework.
Launch a secure cloud migration with PatternBots
If you’re planning to migrate workloads to the cloud and want to build a secure, scalable foundation from day one, PatternBots is here to support you. Our security-first cloud migration consulting is designed to align with your infrastructure goals, compliance requirements, and existing operational workflows. With over 15 years of experience in cloud migration, our cloud consultants can help you identify risks, define migration stages, and implement key technologies like CSPM solutions, EDR tools, SIEM solutions, and Secrets Management. Work with us to reduce configuration errors, improve policy enforcement, and build a cloud environment that’s ready for scale and compliance from the start.Conclusion
The key takeaway here is simple. Security needs to move with the rest of the migration. The more you automate and define clearly, the less you have to fix later. That’s how cloud environments remain stable, compliant, and ready for the next phase of growth. These six steps will help you create a structure where policies are active, systems respond automatically, and risks are handled early.- For a secure cloud migration, start with a clear framework that aligns security with business goals. You should also prioritise visibility across systems, automate policies early, secure sensitive data with key management tools, and validate all configurations with a reliable CSPM solution before scaling operations.
CSPM helps in identifying configuration gaps, aligning setups with security benchmarks, and reducing misconfigurations. It adds a layer of ongoing visibility and control, which is often missing when migrations move too fast without automated monitoring in place.
EDR provides real-time visibility into endpoint activity, which is crucial during deployment. It prevents unauthorised access, flags unusual patterns, and ensures each virtual machine or container is covered with automated threat response mechanisms from day one.
SIEM systems make it easier to track activity across workloads, systems, and services. By collecting and correlating logs from every source, they offer a central way to detect anomalies, streamline incident response, and support compliance reporting in one go.
Lack of visibility across systems, poor access controls, and underestimating policy enforcement are some common risks that organisations face during cloud migration. Many teams also struggle with fragmented tools and disconnected monitoring, which often leads to reactive rather than proactive security measures.