
- Posted on
- Bhanu Pratap
More and more businesses are switching to cloud computing for their cybersecurity needs, making it important to use AI to catch any weird activities. Traditional methods often miss the mark and don’t provide real-time insights, but AI can seriously boost fraud detection, make things more efficient, and help with better decision-making, which all leads to improved performance overall.
When it comes to cloud security, it’s all about keeping the cloud systems safe and making sure data stays private across different online setups, apps, and platforms. Both cloud providers and their customers have to work together; customers need to know their part in keeping things secure and building trust. Teamwork is essential for strong cloud security.
What Is Cloud Computing?
Cloud computing lets people save and access their data and programs on remote servers via the Internet instead of relying on personal computers. It means you can use resources as a service online. Users can store a lot of things, like files, pictures, and documents. Plus, cloud computing and cyber security ensure that you can easily access those resources without worrying about threats.
Here are some key functions you can perform with cloud computing:
- Storing, backing up, and recovering data
- Accessing software on demand
- Developing new applications and services
- Streaming video and audio
How does cloud computing work?
Cloud computing helps users easily access computing resources like storage and processing over the internet, not on local hardware.
Here’s a brief overview:
- Infrastructure: Cloud computing relies on remote servers hosted on the internet to store, manage, and process data.
- On-Demand Access: Users can access cloud computing resources as needed, scaling up or down without needing physical hardware.
- Types of Services: Cloud computing offers benefits like cost savings, scalability, reliability, and accessibility. It reduces initial costs and improves efficiency.
How secure Is cloud computing?
Cloud computing is a go-to choice for many businesses because it’s flexible, saves money, and is super convenient. There are still quite a few worries about security when it comes to using the cloud. So, just how safe is it? A solid cloud provider will offer strong security measures like encryption, firewalls, and systems to catch intruders and keep your data safe. Still, keeping your cloud secure is a team effort. That means businesses also need to make sure they set things up right, control who has access, and handle data carefully. This involves using strong passwords, regularly updating security tools, and keeping an eye out for anything unusual.
Most cloud service providers are serious about security, and they conduct checks and maintenance. It’s really in their best interest to keep things secure to keep their current clients happy and attract new ones. Sure, there are security risks with cloud computing, but those risks can be reduced by teaming up with a reliable cloud provider, putting strong security practices in place, and regularly checking for any vulnerabilities. Right now, the big players in the web services game are Amazon Web Services (AWS) and Azure because they have the certifications and compliance needed for things like SOC 2, HIPAA, GDPR, PCI-DSS, and more basically, they’ve got your regulatory needs covered. By getting a grip on potential risks and using the right security measures, businesses can take full advantage of cloud computing while keeping their sensitive data safe.
What is cyber security all about?
Cloud computing and cyber security protect systems, networks, and programs from digital attacks. These attacks include trying to access, change, or destroy sensitive information, extort money through ransomware, or disturb normal business operations.
A strong defense against cloud security threats includes several layers of protection for computers, networks, programs, and data. A unified threat management system can help organizations automate tasks and speed up security processes like detecting, investigating, and resolving issues.
What are the security risks in cloud computing?
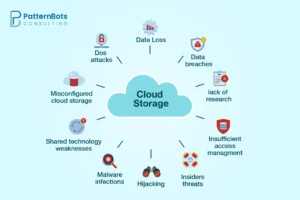
A major security risk in cloud computing is the chance of data breaches and unauthorized access. Public clouds can attract hackers because they store large amounts of data. Organizations need to protect against these threats by implementing strong network security measures, regularly updating security tools, and monitoring for suspicious activity. Compliance issues and insecure APIs are also important concerns in cloud computing and security.
Some key security challenges in cloud computing include:
Limited visibility
Lack of visibility is a major issue for cloud security in cloud computing since organisations frequently do not have sufficient insight and control over their data and systems stored in the cloud. This situation can make businesses open to security problems and misconfigurations.
Data loss
Data backups play an important role in protecting against data loss. Although cloud security in cloud computing solutions is usually dependable because of its distributed systems. There is still a risk of data loss, especially from ransomware attacks that may encrypt or erase significant files.
Compliance issues
Organisations need to comply with regulations specific to their industry concerning Personally Identifiable Information (PII), including HIPAA and GDPR. Challenges in cloud computing and security involve making sure that appropriate access controls and protective measures are established.
Cybercriminals
Cybercriminal activities are increasing, as the FBI’s 2022 Internet Crime Report reveals a 69% rise in incidents compared to the prior year. In 2022, cloud-based apps were used in more than half of malware attacks. This shows how important security as a service(SECaaS) is to cloud computing.
Insecure integration and APIs
In cloud computing, weak APIs and integrations create serious security threats. Systems may risk breaches if they use outdated protocols and the same API secret keys.
Cloud computing and cyber security
| Aspect | Cloud Computing | Cyber Security |
| Definition | Delivery of computing services over the Internet. | Protection of digital systems, networks, and data from cyber threats. |
| Key Focus | Computing resources like storage, networking, and applications. | Securing data, applications, and infrastructure from cyber risks. |
| Deployment Models | Public Cloud, Private Cloud, Hybrid Cloud, Multi-Cloud. | On-premises security, cloud security in cloud computing, endpoint security. |
| Service Models | IaaS, PaaS, SaaS. | Security as a service in cloud computing, Network Security, Application Security, and Data Security. |
| Cloud Computing and Security Risks | Data loss, service downtime, misconfigurations. | Malware, phishing, ransomware, unauthorised access. |
| Cloud Computing Security Concerns | Shared responsibility model, compliance issues, access control. | Evolving threats, insider risks, and lack of cybersecurity awareness. |
| Best Practices | Data encryption, identity and access management, compliance adherence. | Firewalls, multi-factor authentication, real-time threat monitoring. |
| Emerging Trends | Edge computing, serverless architecture, AI-powered cloud management. | Zero Trust Security, AI-driven threat detection, Secure Access Service Edge (SASE). |
Cloud computing security solutions
Security challenges in cloud computing rised due to limited visibility, evolving cyber threats, and misconfigurations. Businesses can implement cloud security services in cloud computing, such as data encryption and threat intelligence, to minimize risks. Cloud security in cloud computing involves proactive monitoring, access controls, and AI-powered anomaly detection.
Cloud computing security solutions include:
- Data encryption – Encrypt data at rest and in transit.
- Identity and Access Management (IAM) – Restrict access to authorized users only.
- Regular Security Audits – Conduct periodic security assessments.
- Threat Detection and Monitoring – Utilise AI-based monitoring solutions.
Which has more market demand: cloud security or cybersecurity?
The demand for cyber security for cloud computing has surged, with increasing threats targeting cloud environments. Cloud security in cloud computing faces two main challenges:
- More advanced cyberattacks are happening.
- There is a lack of skilled security professionals.
By 2032, the cloud security services in the cloud computing market are expected to grow to $123.3 billion, with an annual growth rate of 24.4%. Companies in cloud computing and cyber security will likely offer more service packages to meet this increasing demand. Currently, there are over 8,000 jobs listed for Azure Security on the Indeed jobs site, showing a need for security experts skilled in Azure and AWS as the cloud market expands.
In 2021, the global cyber security for cloud computing market was valued at USD 184.93 billion and is predicted to grow by 12.0% each year from 2022 to 2030. The rise in online shopping, cloud computing, and security challenges, and evolving threats highlight the growing demand for cybersecurity solutions.
Cybersecurity benefits for cloud adoption
Modern cloud computing security solutions, including AI-driven monitoring and zero-trust security, help protect sensitive data. Migration to the pubic cloud has cyber risks, but strong security technologies can help organisations maximise benefits:
Visibility and control in a centralised setting
It helps security teams monitor and respond to threats holistically across workloads, applications, and user activities on the cloud, offering security teams a single pane of glass to monitor activity over time and respond as needed.
Cost savings
Dedicated cloud security is less costly in minutes & operation than onsite equivalents, as they use efficiencies of the cloud for cash and need fewer experts.
Defending against emerging threats
Top cloud providers leverage machine learning and up-to-the-minute threat databases to promptly identify malware and safeguard workloads.
Streamlined compliance
A cloud security platform can provide these and more features, such as continuous monitoring and automated policy enforcement, and help you stay compliant with industry standards.
Reduced impact of attacks
Techniques like micro-segmentation and containerisation lower risk and enhance recovery speed, minimising damage, and data loss.
Data encryption
Encrypting sensitive data in transit and at rest protects against unauthorised access and insider threats.
Access controls
Identity and access management technologies control user access based on roles, and zero-trust models improve security.
Conclusion
Cyber attacks are becoming more common and are a serious concern. No data storage system is completely safe because cybercriminals target both large companies and small websites that hold sensitive information. To reduce risks, both governments and companies focus on protecting their data.
Cybersecurity and cloud security both focus on keeping data safe, but they tackle different problems. Cybersecurity seeks to protect information from attacks like hacking and malware. It works to prevent unauthorised access and reduce weaknesses. At the same time, cloud security keeps data stored online safe from accidental or harmful exposure. Together, they form a defence against growing threats.
At PatternBots, we offer AI solutions to help businesses manage complex data security issues. Our advanced technology accurately detects unusual activities, providing useful insights for spotting fraud, improving operations, and predicting future trends. Whether you want to boost cybersecurity or enhance cloud security, our AI solutions help you stay ahead of threats.
Ready to explore how AI can enhance anomaly detection? Let’s have a conversation.
Frequently Asked Questions
Cloud computing can improve cybersecurity by providing security features like encryption, access management, and constant monitoring. However, it also brings risks such as data breaches, misconfigurations, and unauthorised access. To reduce these risks, organisations should use strong security measures like zero-trust models, multi-factor authentication, and regular audits.
Security as a Service (SECaaS) is a way to get security help from the cloud. Third-party companies provide security solutions like detecting threats, managing firewalls, controlling identities, and monitoring compliance. This approach reduces the need for physical security equipment while keeping protection against cyber threats ongoing.
Businesses can enhance cloud security by:
- Implementing strong access controls and multi-factor authentication.
- Encrypting data at rest and in transit.
- Regularly updating and patching systems.
- Conducting continuous security monitoring and audits.
- Using AI-driven security tools for threat detection and response.
Cloud security services protect data through:
- Encryption: Securing data to prevent unauthorised access.
- Access Management: Implementing role-based controls and zero-trust security.
- Threat Intelligence: Using AI and machine learning to detect anomalies.
- Compliance Management: Ensuring adherence to industry standards like GDPR, HIPAA, and SOC 2.
Here are the best cloud security solutions:
- Identity and Access Management (IAM): This tool manages who can use your cloud resources and how they log in.
- Cloud Security Posture Management (CSPM): This service finds mistakes in your cloud setup and checks for compliance issues.
- Extended Detection and Response (XDR): This solution helps detect threats across different cloud environments.
- Zero-Trust Security Models: This approach limits access by continuously checking user identity.
- AI-Powered Anomaly Detection: This technology uses machine learning to spot and address risks early.